In the previous article, Anatomy of a cyber attack- ICS Cyber Kill Chain-Part 1– we briefly went through the phases of a cyber attack and how an adversary can select their targets, initiate attacks, etc. The Cyber Kill Chain helps Cyber Security organizations and companies to understand a cyber attack from an adversary’s perspective and helps them to grasp a cyber attack in detail. MITRE® has released its version of ATT&CK knowledgebase covering tactics and techniques used in attacks against Industrial Control Systems.
ICS ATT&CK Matrix
ATT&CK for ICS knowledgebase provides critical infrastructure companies and other security organizations with information about the most common ICS application and protocols which can be exploited by adversaries. MITRE®’s ATT&CK framework is widely used by Cyber Security professionals and organizations to check whether their defenses are good enough to detect and block attacks. Security vendors use this framework to check their products against the detection of specific attacks.
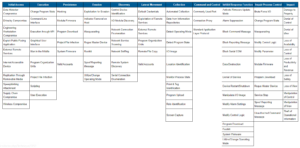
The Cyber kill chain explains the phases/stages of a cyber attack and how adversaries can achieve their goal using different tactics. The ATT&CK for ICS provides Tactics, Techniques, and Procedures (TTPs) based on real world observations of adversaries. It contains information about 11 different tactics and 81 techniques that adversaries can use to achieve their goal in the ICS environment.
Example Tactic and Technique in relation to a Cyber Attack- Stuxnet
The initial access to the plant or a system can be gained through a phishing process targeting someone who corresponds with people working at the victim’s organization. Once the attacker is in the network, they can start injecting the malicious code or initiate other attacks. There are different ways to gain access to the plant network. In an ICS environment, there are few entry points from the IT network to the OT network such as remote access, internet accessible device, wireless access points, etc. Upon gaining access to the production environment, the adversary has multiple ways to cause enough damage. Attacks like Stuxnet where the adversaries infected the ICS with a different program code depending on the target system (MITRE Tactic- Impair Process Control, MITRE Technique- Program Download) to cause the fast spinning centrifuges to tear apart, which turns to be the last action. But before this disastrous event, the adversary exploited every possible flaw or vulnerability in the system such as Zero-day flaws. Most importantly, the whole event went under the radar as the adversaries used rootkit to hide from any possible cyber security counter measures. This raises a question about the counter measures in place.
How can we decide on Counter Measures?
Different Malware serves different purposes in a targeted attack; intrusion, data theft, destruction, and more. To a threat actor, maintaining a presence in a victim’s system is crucial. They need to be able to give commands continuously to their malware. This communication is usually called command and control (C&C) server where malware has the highest priority. The attackers update their malware regularly to stay ahead of their corresponding security countermeasures. So, deciding on the counter measures is a significant step in designing the overall security concept of the plant. Starting from selecting the hardware for the engineering stations to the firewall between the IT and OT network, the ICS Threat modelling helps organizations to identify the attack surface and the corresponding risks. It allows a cross functional cooperation between the IT and OT stakeholders. This allows scaling the threat modeling across all devices, software applications, protocols of the ICS environment. Ultimately, the organizations can improve their approach towards Cyber Security starting from the design- “Security by design”.
Constant testing and improving the Counter Measures
Frameworks such as ATT&CK for ICS help Cyber Security organizations and professionals to understand and evaluate the cyber attack and also to describe the post-compromise adversary behavior. The counter measures that are already implemented may no longer be valid or not sufficient enough to prevent and detect an attack if there is no regular validation. As an example, a regular anti-virus signature update is important to prevent against the zero-day threats, a firewall firmware update against its vulnerability, regular security updates of workstations, etc. Therefore, constant validation of counter measures is equally important apart from deciding and implementing them.
The ICS ATT&CK Matrix provides an extensive overview of different cyber attacks that can be targeted towards the ICS by the adversaries. The importance of choosing the countermeasures for a specific attack is pivotal to reduce or avoid the damage caused by adversaries. The mitigations mentioned for each technique listed in the matrix can help security organizations and professionals to a greater extent. It helps ICS Vendors and customers to gain insights about the different techniques used by the adversaries to gain access to the system, thereby helps them to decide on the counter measures. Preparing for any cyber attack involves extensive planning of budget and resources.
Are you prepared to face a cyber attack? If not, do not hesitate to contact us via our contact page. We’re happy to support you.




