Digital ambition – key aspect Plant Security
As the world becomes increasingly connected, smart, sustainable growth hinges on the ability to adapt to customers’ changing needs – quickly and efficiently. Businesses can achieve this in a shrewd way with appropriate innovations such as digital tools.
Plant Security Touch
To ensure that technical innovations are successful, companies must make an acute focus on people and Plant Security as top priority from now on. There are no other alternative to this!
‘Business as usual‘
Plant Security and safety must be firmly integrated in the corporate culture as part of the daily business.
Chee Hoe Lee, General Manager Strategic Business Global IA Cyber Security Evangelist, Yokogawa Engineering Asia Pte Ltd, was subsequently available for questions on the topic in an interview:
Mr. Lee, in today’s smart world, do your business operations still follow certain maxims?
Chee Hoe Lee: Yes, definitely. Place the focus on people. The maxim is this: we have to have a shared fundamental understanding and develop a strategy that sets out where we stand, what our basic attitude is, what corporate culture we observe and how we want it to evolve.
With regard to cyber resilience, businesses are meanwhile under strong pressure to permanently raise their employees’ awareness of cybercrime. People must be provided with a basic understanding of the methods and procedures used by cybercriminals – what we call social engineering – through special Cyber Security awareness trainings. That way, they’ll be better equipped to recognize attempted scams and react accordingly.
Plant Security is a typical key enabler, along with the human factor, for the successful implementation of innovative technologies. Why’s that?
Lee: Plant security is an important factor for the use of innovative technologies because the expanded connectivity and interaction of manufacturing processes mean secure and resilient communication lines are a must – as shields to avert danger from the company, as it were. As digitally networked production continues to make inroads, the risk of cyber attacks is increasing and with it the need to protect industrial control systems (ICS) from the threat of financial, reputational consequences due to production downtimes, damaged machinery, patent theft or cyber extortion.
What Plant Security aspects are currently the most burning issues for businesses?
Lee: In order to rule out risks to smooth business processes, the management must weigh up all factors carefully. A business impact analysis (BIA) and risk analyses are normally carried out concurrently and in concert, so as to obtain robust results. Only then can the impacts of disruptions on business operations due to cyber security risks and likelihood be fully assessed.
A business impact analysis (BIA) and risk analysis should ideally comprise the following ingredients:
Asset inventory
An asset inventory is a significant part of a company’s Plant Security strategy. Detailed information is collected on all hardware and software assets – such as DCS/PLC, sensors, actuators, valves, transmitters, firewalls, network routers, switches, computers, servers and printers – including the current state. This inventory serves as a starting point for informed decisions regarding the further development of essential security portfolio infrastructure projects. You can only protect something effectively if you know what it is you’re protecting.
Bow-tie diagram
The bow-tie diagram is a pictorial representation of complex risks, in other words for clarifying risk situations. It provides a valuable structure for applying controls and avoiding security incidents. By visualizing risks clearly in this way, the bow-tie diagram underlines the importance of an OT / IT process for businesses. It is easy to understand – not only for security employees but also for everyone else at the company.
In short, the use of bow-tie diagrams for security creates enormous potential, which can be leveraged to keep a close watch on controls over IP, assets, market shares, revenue and the firm’s reputation.
In addition, Bow-tie diagram can also be applied to Safety risk assessment. Since Safety and Security are closely inter-wined, it can help to harmonize the approach.
Threat modeling
Threat modeling enables potential threats such as structural weaknesses to be identified, listed and prioritized in relation to hypothetical cyber attacks. It supports the establishment of a comprehensive security architecture with an appropriate security level and helps minimize the attack surface of the system under examination.
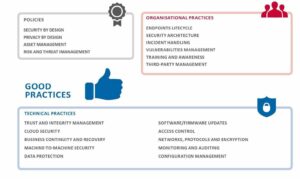
The current ENISA (European Union Agency For Network and Information Security) study makes it very clear, for example, that asset management, risk & threat management, training and awareness are suitable cyber security policies and good practices.
Source: European Union Agency For Network and Information Security, Good Practices for Security of Internet of Things in the Context of Smart Manufacturing; November 2018
https://www.enisa.europa.eu/publications/good-practices-for-security-of-iot




