Almost every industry is traversing the cycle of digital transformation – the mega trend in the twenty-first century! Improved productivity, more flexibility, high customer satisfaction and the establishment of new business models are just a few examples of the numerous potential success prospects which are created. According to a Bitkom study, more than 90% of all companies in Germany see digitalization as a fantastic opportunity. (Document: Digitale Transformation der Wirtschaft (2nd Edition) Berlin, 11 July 2017; page 14)
Digital transformation
Of course, there are also a few uncertainties. The increasing professionalism of cybercriminals coupled with the steady rise in cyber attacks is causing considerable concern in the business world. No wonder – a representative study by Bitkom, Germany’s digital association, in summer 2017 revealed that more than one in every two companies has been the victim of an online attack during the last two years. 53 percent of German firms have been hit by industrial espionage, sabotage or data theft. The damage adds up to some 55 billion euros a year.
The “shotgun” approach
It can happen to virtually anyone – large corporations and mid-market players in every sector of the economy. It’s obviously very tempting for cybercriminals to focus their attacks on companies which simply don’t have the capacity to implement a security concept as sophisticated as that of a multinational group. Yet unfortunately, even the biggest organizations are not immune because many cyber attacks are not targeted but carried out en masse according to the “shotgun” approach. “WannaCry is a good example here – an aggressive ransomware campaign that went viral, so that it was impossible to predict where it would spread to next.
Significance for critical infrastructures (KRITIS)
Critical infrastructures (KRITIS) are organizations and facilities of major importance for society, whose failure or impairment would cause a sustained shortage of supplies, significant disruptions to public order or other dramatic consequences. (Source: BSI)
The availability and security of IT systems plays a central and immensely important role when it comes to critical infrastructures!
A key enabler for the digital transformation – plant security
Plant security is the foundation that is necessary in order to capitalize on the significant opportunities, and master the challenges, presented by digitalization. Innovative, digital business processes can be driven forward agilely, flexibly and above all SECURELY in this way!
Yokogawa’s plant security portfolio
It’s probably crystal clear to anyone that functional safety (IEC 61511) is a “must-have” for safety instrumented automation solutions. However, cyber security – protection against cyber attacks – is no less crucial. There are two different aspects to safety and security which can be differentiated as follows: functional safety refers to the protection of people, equipment and the environment whereas cyber security comprises the availability, integrity, and confidentiality of a plant’s IT components – in exactly the reverse order in industrial automation compared to ordinary IT! The aim is to shield the IT in an industrial plant from cyber threats. A combination of functional safety and cyber security is necessary to achieve holistic protection.
Yokogawa’s plant security portfolio conforms to international standards and recommendations such as the International Electrotechnical Commission (IEC) 62443, national recommendations, e.g. NAMUR (NE) 153 and 163 or the German Federal Office for Information Security (BSI) – especially with regard to critical infrastructures (KRITIS).
All of this is reconciled with your individual requirements as the starting point for the perfect plant safety concept.
IEC 62443
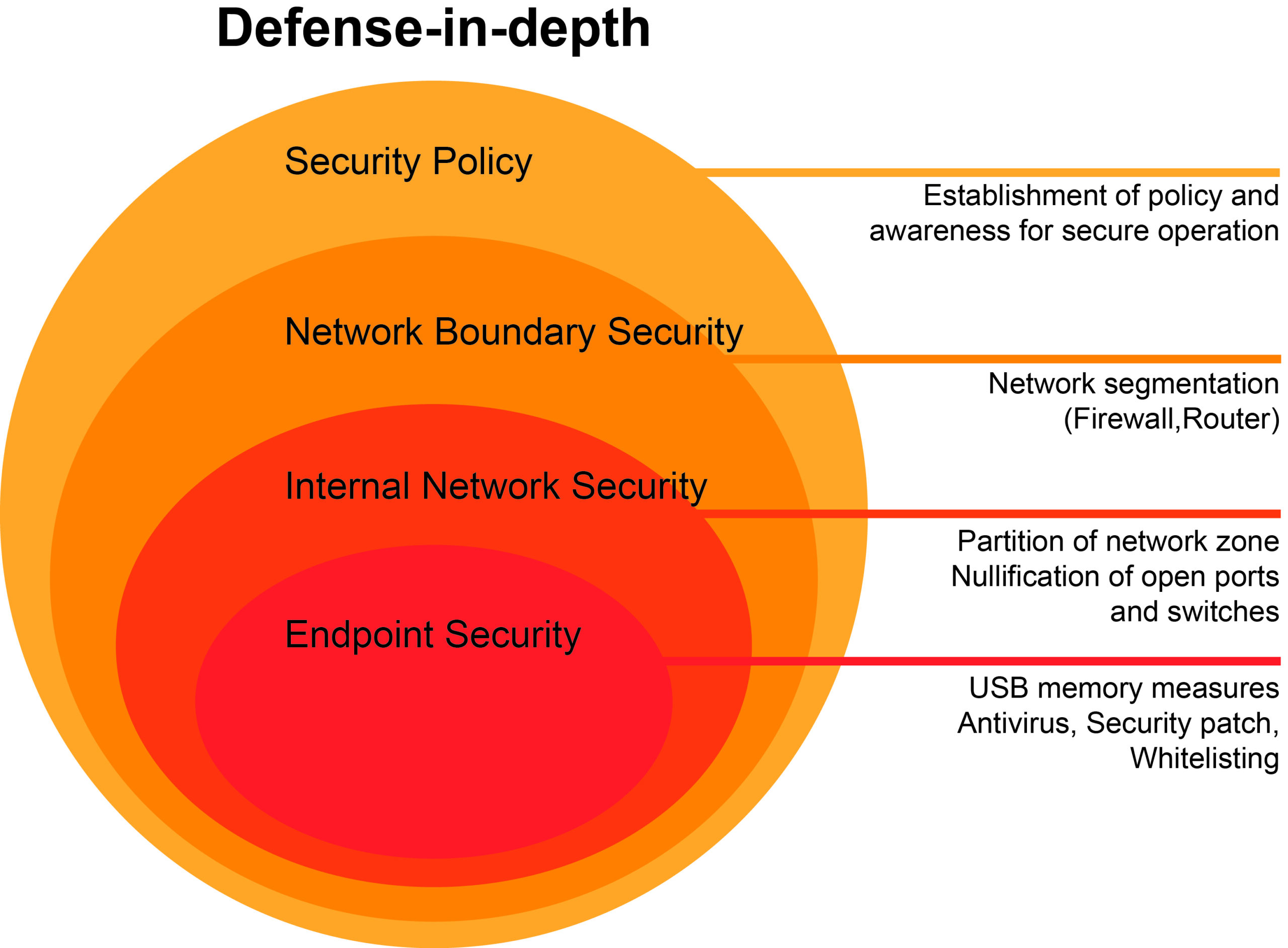
This standard lays the foundation for an integrated view of plant security that encompasses the entire lifecycle of an automation solution. The plant system, including all safety relevant components, must be protected against unauthorized access, so that cybercriminals are left without a target! IEC 62443 also addresses the protection of networks within automation systems. The standard calls for the system as a whole to be partitioned into security zones. Secure conduits are specifically defined between these zones and protected by firewalls. The requirements vary according to the security levels of the individual zones. This structure results in a multilayer system of different defense mechanisms (also referred to as “defense in depth”). The firewalls are hardened according to the required security level.
Defense in depth
“Defense in depth” is the coordinated placement of multiple security mechanisms to protect a company’s databases. This strategy is based on the military principle which states that it is more difficult for an enemy to overcome a complex and multifaceted defense system. Defense-in-depth strategies typically include components such as antivirus software, firewalls, anti-spyware programs, a multilevel password system, intrusion detection mechanisms and biometric recognition systems. Along with countermeasures on the IT side, physical protection of a company’s facilities also makes business critical information more secure against theft or destruction in conjunction with comprehensive, ongoing training for all employees.
NE 163 – Security risk assessment of SIS (safety instrumented systems)
This Namur recommendation represents a practical and minimally disruptive method for assessing IT risks (i.e. the availability of the plant is maintained. A security risk assessment provides a starting point for increasing the resistance of safety instrumented systems to IT threats. Any weaknesses which exist are identified and specific improvements suggested.
The method described here (based on ISO/IEC 27005 and IEC 62443 3-2) checks whether suitable security mechanisms are applied, particularly those defined in IEC 61511-1, VDI/VDE 2180, VDI/VDE 2182, IEC 62443 and the BSI ICS Security Compendium.
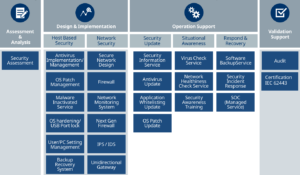
IEC 62443 – the international canon – comprises four key pillars laid down by the cyber security concept: General + Policies & Procedures + Cyber Security Management (System Security + Component Security).
In keeping with IEC 62443, we begin by carrying out the following steps together with you:
- Assessment & Analysis
- Design & Implementation
- Operation Support
- Validation Support
These steps are important in order to comply with international industrial standards (IEC 62443) and eventually be certified. The big advantage for you is that by taking this approach, we establish security compliance at your company. You profit from clear processes which you can leverage to make your business fit for digitalization. Capture this competitive advantage.
Plant security is an issue that concerns the company as a whole.
Are you fumbling in the dark? Profit from our rich expertise in the automation sector. We’d be delighted to inform you how you can realize a 360° security concept featuring state-of-the-art technology in line with international standards and simultaneously increase security awareness at your company, so that your entire organization is optimally protected against both internal and external threats.
Side note: The European legal basis – the General Data Protection Regulation (GDPR)
A few words about the GDPR
We take a holistic view of security. That means we keep a close watch on all current, legally relevant developments and integrate them into our concept accordingly. We’d therefore like to take this opportunity to say a few words about the GDPR:
The General Data Protection Regulation (GDPR) of the European Union is the new, EU-wide regulation on data protection which becomes enforceable on 25 May 2018. It gives more control to citizens and residents over their personal data, creates transparency regarding data use and stipulates security mechanisms and checks to protect information. With just 88 pages, it is a decidedly slender document for a European regulation – but one which will greatly simplify the regulatory environment for businesses within the EU. It applies not only to European companies but also to organizations based outside of the EU: Facebook, Alibaba & Co. must in future abide by this general regulation if they collect or process personal data of individuals located inside the EU. Failure to comply with the GDPR will result in severe penalties of up to 4% of worldwide turnover or €20 million, whichever is higher.
Key questions – Which personal data do you process today?
- Customer databases
- Feedback forms
- Emails
- Photos
- Surveillance videos
- HR databases
- Log files
- Backups / archives
- For what purpose was this data stored?
- Where was this data stored?
- How long is this data stored for?
- Personal data for marketing purposes – prize competitions / Christmas cards / newsletters
If you’d like to learn more about security, click here. We hope you enjoy browsing!




