Imagine this scenario: A chemical processing company decides to launch a cybersecurity program for a manufacturing plant, so it brings together an IT expert and someone from operations who is moderately well versed in the plant networks. The two have other responsibilities and complete their task quickly by inserting a smattering of security appliances at strategic points and declare the plant protected.
Meanwhile, a hacker who has been systematically analyzing the plant’s networks over several months, has a better grasp of the architecture and what assets are deployed than anyone in the facility. The hacker gained access because some system integrator, a few years ago, installed a Brand X PLC to solve a chemical injection problem. The technician left a path to access the PLC via the internet for follow-up service, but everyone has forgotten about it. The hacker is aware of a key vulnerability—a default password—with that PLC because its characteristics were published, but the plant never acted on changing it because they had forgotten it is even there. This vulnerability provides the hacker a path into the larger network through an unprotected connection from the PLC to the automation system.
While this scenario is an oversimplification, it illustrates the problems many companies face as they consider how to approach cybersecurity strategy for operations technology (OT) networks. A well-thought-out strategy will find and correct these problems, and for the rest of this article, we will look at how to implement this type of plan.
An evolving attack surface
Much has been written about the convergence of IT and OT, and how the extension of IT technologies into OT networks has expanded the attack surface, but also brought new defensive tools.
Most older plants used to be completely isolated but are now connected to the outside world via company intranets and/or the internet, likely in more ways than most people realize. Companies are striving to transform their operations and businesses digitally for competitiveness by connecting not only vertically within their plant, but also horizontally within sites, with other sites, and across the supply chain. These connections create business opportunities, but also create challenges in securing the network and data.
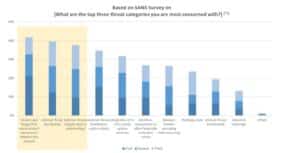
With more components and functions required to optimize the larger operation, plants are becoming increasingly complex and automated, with use of commercial technologies like Windows, Ethernet, and TCP/IP. Research shows that the top three cyber threats are devices and “things” added to the network (such as the PLC in our opening example), internal threats (human negligence or accidents), and external threats (supply chain or partnerships). IT and OT convergence has brought mixed results, helping some defensive efforts and hurting others depending on the situation (Figure 1).
Figure 1: Leading cyber threats compiled by the SANS Institute in its 2019 State of OT/ICS Cybersecurity Survey.
OT’s natural resistance to change
Those responsible for OT networks do not always welcome help from the IT side. If something works and is necessary to ensure uninterrupted production, even if old and not well protected, the usual answer is, “Don’t touch it.” The tools and upgrades that IT wants to bring to the plant may be incompatible with older equipment and software, causing production interruptions and even compromising safety. On the other hand, malware can do the same things, so IT feels the need to get involved. However, simply importing IT security technology and policies into an OT environment to improve OT security does not work because IT security is driven by different requirements and priorities.
IT must understand that an industrial control system is the brain of the plant. Its availability, resilience, and sustainability affect the availability of the entire plant—as well as safety, operational cost, and business performance. Anything interfering with its performance impacts the corporation, top management, and stakeholders.
In light of this situation, security risk management is a top priority for organizations and responsible teams in spite of serious challenges:
- Assessing risk of low visibility OT assets—Plants evolve over the years, and like the PLC in the opening example, many are not good at documenting changes, nor do they drill down into the infrastructure looking for potential vulnerabilities.
- Mitigating risk and prioritizing investment—When companies have little visibility into their OT assets, it is difficult to project how much investment is needed for security or where the effort should begin. Moreover, it will be impossible to know how much risk was reduced by the effort.
- Keeping up with industry standards—Implementing countermeasures and continuing to be compliant with emerging standards is challenging. More on that in a moment.
- Managing risk with limited OT security expertise—While implementation and management of security measures must continue throughout the plant lifecycle, which lasts for more than 20 years, security teams often face a lack of security personnel and expertise.
Risk-based approach
There are two general approaches to reduce risk. The maturity-based approach builds the highest level of defense around everything. It is the most comprehensive but very expensive. The risk-based approach optimizes defensive layers for risk reduction where it is needed most. This sacrifices some coverage, but is far less expensive and easier to implement, and thus much more likely to happen.
Risk-based security depends on four practices:
- Determine the security baseline: The first step is a risk assessment to identify risks and enable OT security stakeholders to understand the baseline. Acknowledging the current status of the plant is fundamental and is the starting point of the security journey.
- Define risk from a holistic view: Risks come from many different directions and categories, so a risk assessment that only focuses on high-level business processes might fail to identify risks due to flaws in technical implementations. Insufficiently defined security leadership in the boardroom is a risk, but so is a poorly configured firewall. Therefore, it is essential to have a scope that is sufficiently broad and incorporates different parts of the organization. Furthermore, a combination of a paper review with an onsite, technical assessment is vital for a comprehensive risk assessment.
- Comply with security standards for guidance: Compliance with a security standard is beneficial since it makes the implementation of a security program more effective and straightforward, as compared to reinventing the wheel each time.
- Establish a systematic process: Organizations must follow a systematic process to establish a persistent operational risk management process for OT security. This risk management process is a strategic activity that involves short- and long-term considerations. Thus, planning for strategic risk management is necessary to ensure continuous risk assurance.
Security standards
As just mentioned, a key element of risk-based security is compliance with relevant standards. A plant setting up to manufacture cheese has to comply with applicable regulations rather than its own definitions of sanitation. In the same way, cybersecurity has its own practices and guidelines to help companies. Growing numbers of companies are working to:
- ISA/IEC 62443
- NIST CSF (Cybersecurity Frameworks)
- NIST 800-82
- CIS Critical Security Controls.
- ISO 27000 series (Mainly used in IT)
There is no single regulation, standard, or best practice covering all aspects and regions. In the case of Europe, the European NIS (Network and Information Systems) directive has been rolled out and will result in laws passed on a per country basis.
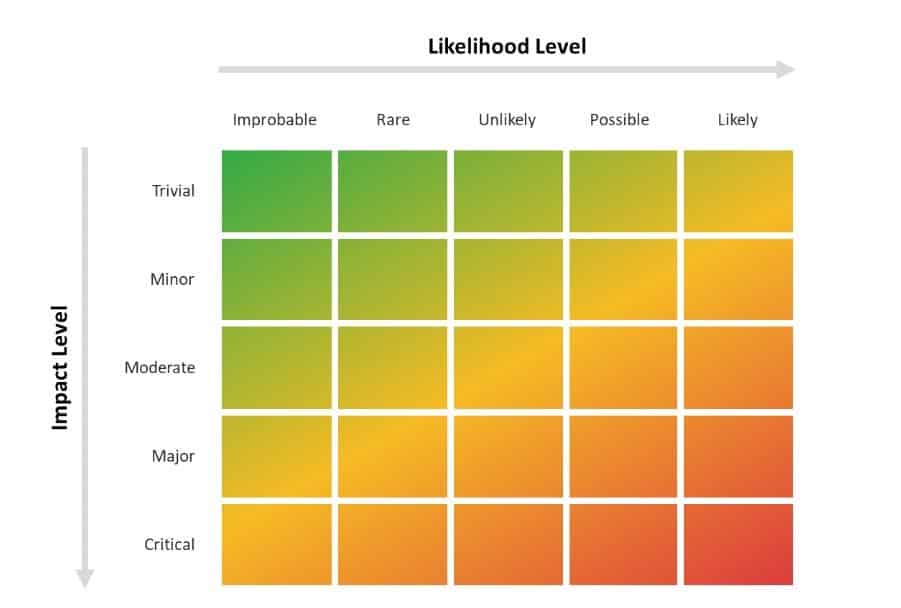
Arguably, the most important standard on the list above is IEC 62443 since it is designed specifically for industrial systems and covers every aspect of a security program, ranging from risk assessment to technical design specifications. Its approach defines a target security level for a plant or zones of a plant (Figure 2). Companies are required to establish the correct target security level when assessing their plant.
Figure 2: Security levels based on descriptions in IEC 62443-3-3
Additionally, IEC 61511, a technical standard setting practices for engineering safety instrumented systems (SISs), explicitly states that conducting security risk assessments is now a mandatory requirement.
First step: Risk assessment
As the first step to risk-based cybersecurity management, Yokogawa recommends a technical security risk assessment (TSRA) as the starting point to obtaining the OT security baseline. By assessing the impact and likelihood associated with threats facing the OT environment, a TSRA determines the security risk to the organization.
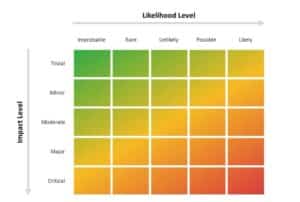
Yokogawa’s TSRA process starts with a vulnerability assessment based on customer interviews and technical inspections. When vulnerabilities are identified, a scenario-based risk assessment is conducted to define the highest risks facing the OT environment, and which problems need to be solved most urgently. Vulnerabilities and risks are not the same (Figure 3). A vulnerability is a flaw or weakness, while a risk is the probability of something bad happening. Returning to the opening example, the vulnerability is the default password. Another typical vulnerability can be lack of bounday protection. The risk is what can happen if the hacker leverages the vulnerability.
Figure 3: Each Vulnerability must be examined in light of the probability that it could be used maliciously.
In the technical vulnerability assessment phase, multiple methods are used to gather vulnerabilities, verify and check findings, and create a complete and reliable list of those existing in the environment. The list becomes the input of the risk assessment phase conducted by the same team that was involved in the vulnerability assessment phase. This means that a large amount of knowledge and insight regarding the vulnerabilities will be present at the start of the risk assessment.
The technical risk assessment concludes with a report that includes:
- A list of risks and vulnerabilities
- Findings on any high-level risk and immediate actions required
- A gap analysis between the existing state of the plant and security requirements
- A roadmap showing how to develop or improve the security program, including plans for countermeasures and other concrete recommendations.
Assessment methodology
Consultants and engineers perform the vulnerability assessment together using several methods, including interviews and technical inspections.
Interviews work through an extensive questionnaire based on both the IEC 62443 and Yokogawa’s extensive security experience. The questions vary from detailed technical implementation to how security is managed by the local organization. Answers to these questions are integrated with technical inspections, including user and PC management, network device inventory, patches, updates, and antivirus management.
Each vulnerability must be examined to determine the risk it presents, which is a combination of how much damage an intruder could do by using a vulnerability and the likelihood of the intruder actually carrying out a damaging action. The combination of impact and likelihood becomes the risk level (Figure 4).
Figure 4: All attacks vectors are not the same, so the defense must reflect the risk level.
The result of the vulnerability and risk assessments are documented in the TSRA Report that contains:
- Executive summary
- Methodology overview
- Risk overview for the OT environment
- Vulnerability overview for the OT environment
- Gap analysis between the plant’s existing state and security requirements
- Roadmap on how to develop or improve the security program.
The outcome of the assessment will support constructive discussion with management on what immediate measures need to be taken to address the high-level risk, and how to plan an effective security program to implement countermeasures. The ultimate objective is a program that runs continuously and is constantly evaluated and improved as threats and tools evolve.
Adopting a risk-based approach will guide organizations to make complex decisions, choose which action to take, and where to invest. Effective risk management starts with knowing and thoroughly understanding company- and plant-specific risks. However, the complex operational environment, evolving cyber threats, and continuously updated laws and policies make this responsibility extremely challenging for organizations to handle internally.
Since this can be challenging even for the most experienced professionals, many companies seek support from security partners when it comes to security assessments. With in-depth knowledge and vast experience in both plant operation and OT security, Yokogawa’s consultants and engineers can serve as guides along the security journey.
Real-time, Model Based Digital Twin for Energy and Emissions Management