Cybersecuirty policies and procedures are fundamental to define the security goals of the organization and describe the workflows to achieve these goals. However, integrating IT security with OT security can be difficult in defining and executing a unified security strategy. IT security is generally focused on confidentiality of data whereas OT security focuses on the availability (uptime) and integrity of data. Therefore, when designing cybersecurity policies & procedures for ICS (Industrial Control Systems), these priorities must be correctly understood and combined to form an effective security program following industry guidelines.
How does Yokogawa ensure defined policies & procedures to be in place and apply effectively to avoid any gaps between people, process and technology?
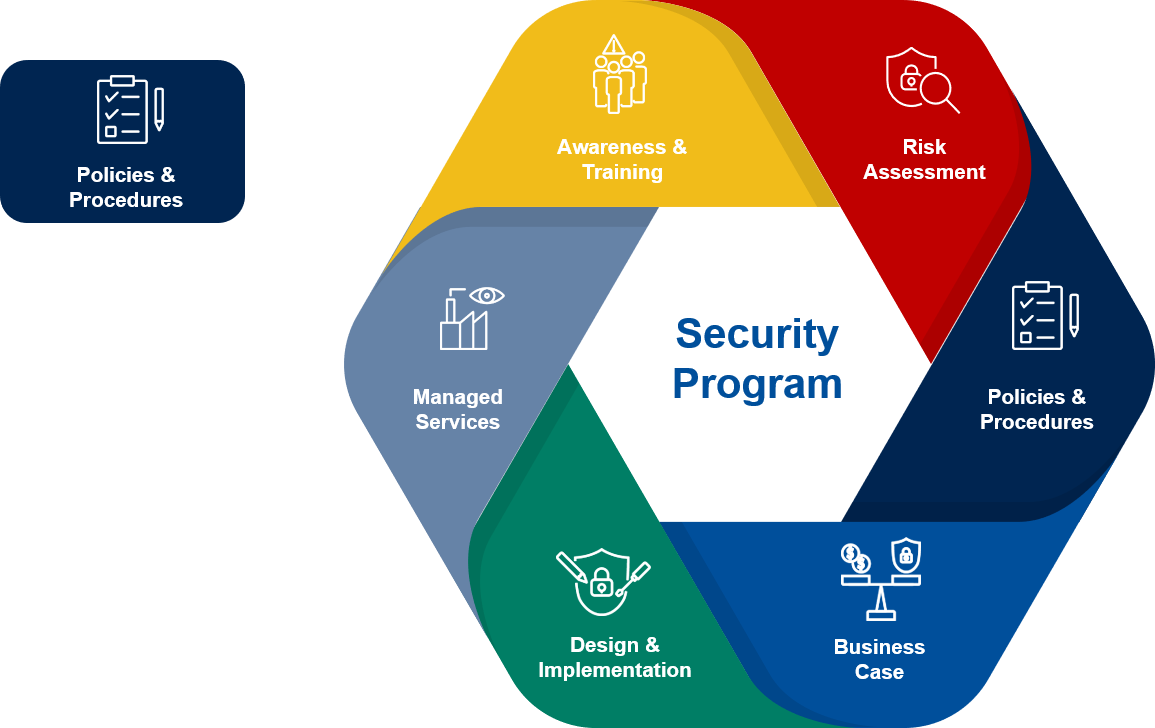
Following the established Yokogawa’s Security Program, after completing the cybersecurity risk assessment and understanding the customers’ security status as a 'baseline', the next step is to define the security goals within cybersecurity policies. The statements in the policies act as the foundation for the procedures, which describe the workflows to securely operate and maintain customer's control systems.
Yokogawa’s developed policies and procedures, bridging gaps between people, process and technology, cover areas such as:
• Asset management
• Access control
• Incident management
• Business continuity plans
• Compliance management
• Communications management
• Security system maintenance
Yokogawa’s cybersecurity consultants can advise the best course of action towards developing or improvement of company's policies and procedures based on a set of predefined policy and procedures templates available in accordance with our best practices and the IEC 62443 standard.
Customer benefits of having a set of well-defined cybersecurity policies & procedures
Having a comprehensive set of cybersecurity policies and procedures, following international rules and industry guidelines, will increase the security status of your organization. Using industry best practices developed over many years of experience, our cybersecurity experts make sure
- To develop the most effective strategies for effectively communicating policies, standards, and procedures for measuring good security practices and compliance.
- To create customizable OT cybersecurity policies and procedures to expedite the development of security documentation according to your organization’s specific requirements.
- To keep staff up-to-date on industry cybersecurity standards and recommended practices.
- To provide ongoing management of your policies, procedures, and standards to ensure those documents are kept current and relevant.

Looking for more information on our people, technology and solutions?
Contact Us
